Here’s how to check if your Android device is vulnerable to the dangerous Broadpwn WiFi exploit in the Broadcom wireless chips.
Android’s July security update included no fewer than 138 fixes and 18 of those were classed as RCE, or Remote Code Execution, meaning a person could remotely execute code if the right conditions were met.

One of those fixes was for a flaw in Broadcom’s Wi-Fi code, which just so happens to be used in a lot of devices that are powered by Android. That vulnerability has now become known as Broadpwn, and fortunately for us, there’s an app that can check your Android device and report back whether it is at risk from it.
The WiFi Chipset INFO app, available as a free download from the Google Play Store, does one thing and one thing only, but it does it very well indeed. Once installed and fired up, it goes away and checks exactly which WiFi chipset you have in your device, confirming the manufacturer and finally whether your device is at risk from Broadpwn. Hopefully, you will not be, and you should have little to fear if your device’s manufacturer has been quick on the draw with security updates.
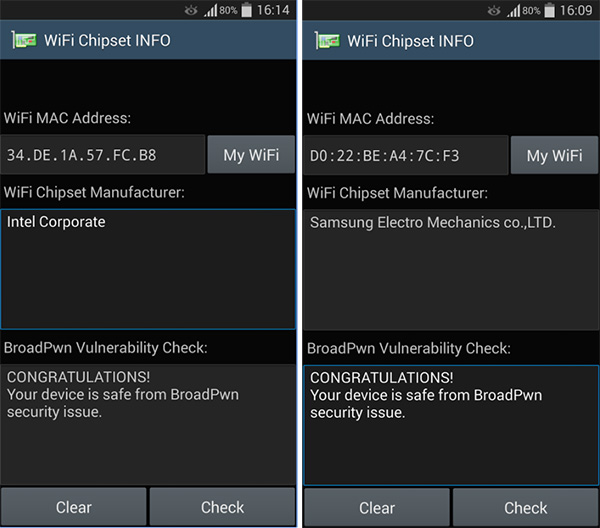
If you are at risk and want to have a read through the full explanation of the Broadpwn situation, you should know that the nature of the risk involved isn’t for the feint of heart. The way we understand it, the vulnerability allows malicious data to pass through your network and into your device when it is connected to WiFi. Attackers can use this to have as much control over your device as the Android system itself.
That’s enough for us to know this bug needs to be patched, and quickly. With Samsung’s latest devices, including the Galaxy S8 and even Pixel phones using the Broadcom WiFi chips, there are plenty of devices out there potentially at risk!
(Download: WiFi Chipset INFO on the Play Store)
You may also like to check out:
- iOS 11 Beta 5 / Public Beta 4 Download Release Date Expectation Info
- Apple Watch Jailbreak On watchOS 3 Demoed At Def Con
- Download: iOS 11 Beta 4 IPSW Released For Devs, Here Are The Details
- Download: Windows 10 S ISO Files Released On MSDN
- GTA 6 Release Date Tipped After Resume Posted Online Shows The Game In Later Development Stages
- Jailbreak iOS 10.3.3 / 10.3.2 / 10.3.1 / 10.3 For iPhone And iPad [Latest Status Update]
- Download iOS 11 Beta 4 & Install On iPhone 7, 7 Plus, 6s, 6, SE, 5s, iPad, iPod [Tutorial]
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

