A new strain of Android ransomware, which disguises itself as a legitimate application, has been discovered to be utilizing the Extensible Messaging and Presence Protocol (XMPP) for instant messaging, to receive commands and to communicate remotely with the server that controls the malicious installation.
According to a report on this subject, it seems that the new sophisticated methods of communication are paying off for those who are operating the crypto-ransomware attack. Once the seemingly innocent application has been provided with administrative permissions, it immediately goes to work exploiting the Android operating system. The frighteners are then introduced to the end-user when the virus presents itself and claims to have encrypted the users files on behalf of the United States National Security Agency (NSA).

Ofer Caspi of Check Point Software Technologies has presented evidence that not only are the majority of the affected individuals residing within the United States, but that approximately 10-percent of those who have been presented with the ransomware have chosen to hand over a “ransom” of between $200 and $500 to gain back access to their files on the infected device. It is believed that the individuals behind the attack have pocketed somewhere close to half a million dollars from the scam. Although in reality, the actual figure could be significantly higher than this.
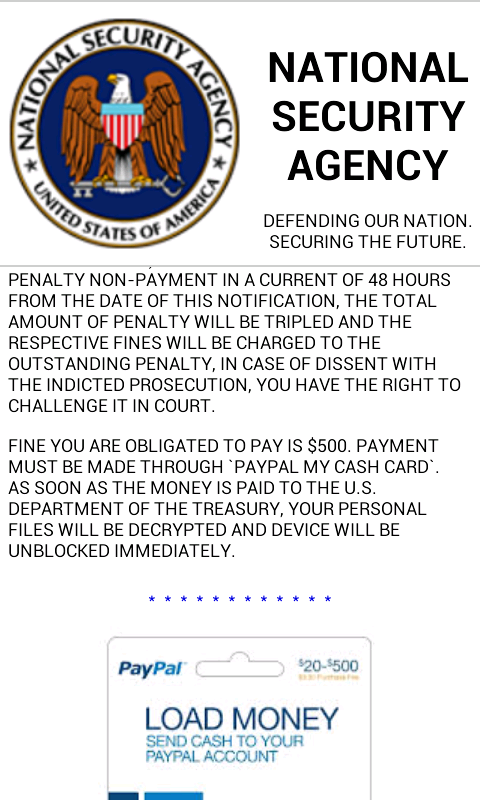
The installation of the infected application seems innocent enough. It works under the pretense that NSA is involved, and seemingly the use of threatening and aggressive language, including threats of fines pertaining to copyright violations has convinced a tenth of those affected to err on the side of caution and pay the ransoms. This isn’t the first time that the NSA insignia has been used to extort money from users, with historical malware such as Koler and Simplocker applying the tactic. Check Point discusses why the use of this tactic through XMPP is so effective:
Using XMPP makes it much more difficult for security devices to trace the malware C&C traffic as well as distinguish it from other legitimate XMPP traffic. It is also makes it impossible to block traffic by monitoring for suspicious URLs.
There’s no doubt that this new strain is a sophisticated, extremely sneaky piece of ransomware. Stay vigilant out there, folks, and remember that agencies such as the NSA will never present this type of message on a device.
(Source: Check Point)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

