iOS may have been threatened by the WireLurker malware which crawled its way into devices via Macs, but at least it was a situation which was contained till China after Apple took measures to counter it. Now we have ‘Masque Attack’, a new threat which replaces legitimate, App Store downloaded apps with ones loaded with malware.
Back in July 2014, it was discovered that when installing an app using ‘enterprise/ad-hock’ provisioning, it could replace a genuine app on your iOS device if it had the same ‘bundle identifier’. The app could display a title it wanted during the installation process, but once on the device, this tricky piece of malware could replace any user-installed app, but not the pre-installed ones from Apple.

FireEye says that it informed Apple about the situation on July 26, but since then, the team of researchers have verified that this vulnerability still exists in iOS 7.1.1, 7.1.2, 8.0, 8.1 and the new iOS 8.1.1 beta. The vulnerability and threat remains alive for both jailbroken and non-jailbroken devices as Masque Attack works through wireless networks as well as USB connections.
WireLurker, that was infecting iOS devices though Macs via USB was also using Masque Attack’s ghosting in a limited form. Where WireLurker was responded to by Apple, after which news and concern spread like wildfire on the Internet, FireEye believes that the threat from Masque Attack is far greater than that which WireLurker poses.
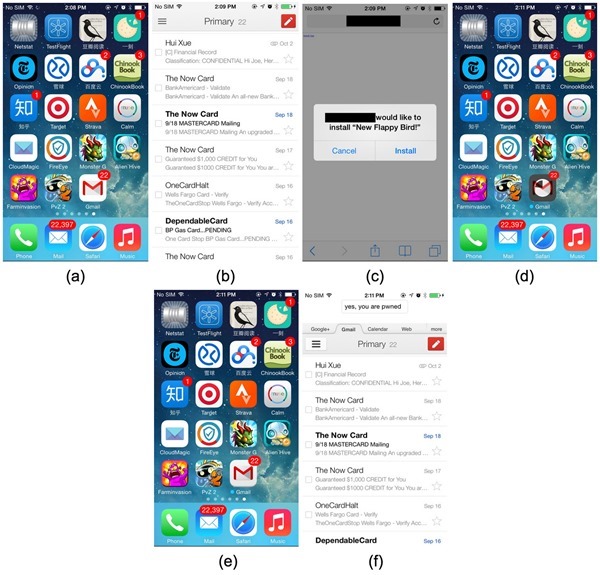
The team says that the malware can replace authentic apps such as banking ones, and replace them with the ones from the attacker. Such apps can even sport the same UI as well as ensuring that the attacker is able to collect all your personal details in the process of you using the app.
Surprisingly, the malware can even access the original app’s local data, which wasn’t removed when the original app was replaced. These data may contain cached emails, or even login-tokens which the malware can use to log into the user’s account directly.
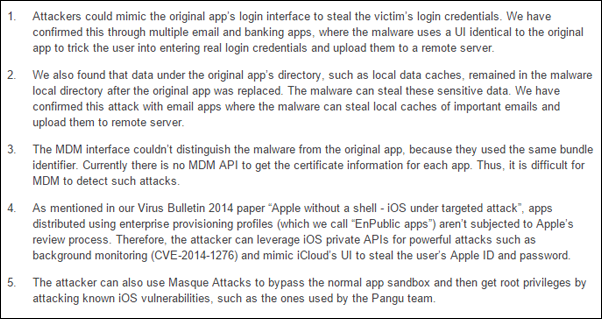
FireEye has also noted down details of the security consequences that Masque Attack can have on infected iOS devices. While these details are too technical in nature, it does paint a picture of the seriousness of this issue and how easy it is for Masque Attack to steal personal information, including financial details from any infected iOS device.
(Source: FireEye)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

