Google Project Zero’s Tavis Ormandy discovered vulnerabilities in uTorrent desktop and web apps that could allow attackers to inject malware or fetch data on previous downloads.
The security researcher revealed that attacks can make their way from malicious websites and through easily surmountable HTTP RPC servers – created by default on port 10000 by uTorrent Classic and port 19575 by uTorrent Web – to infect a target PC with malware or gain access to download history. It seems the 8-byte secret that is meant to protect the RPC servers from remote attacks is easily compromised, and once that is done, the way to the device using the client is laid bare.

The uTorrent Web client is the most severely affected by this security flaw, with attackers able to change the default download directory of the client (to the /Startup folder, for example), write files to said directory, and gain access to data including settings, crashdumps, and logs.
With uTorrent Classic, Ormandy was only able to fetch download history and previously downloaded files still in storage, though that is still quite a cause for concern despite being much less serious than the vulnerabilities plaguing its web counterpart.
This requires some simple dns rebinding to attack remotely, but once you have the secret you can just change the directory torrents are saved to, and then download any file anywhere writable.
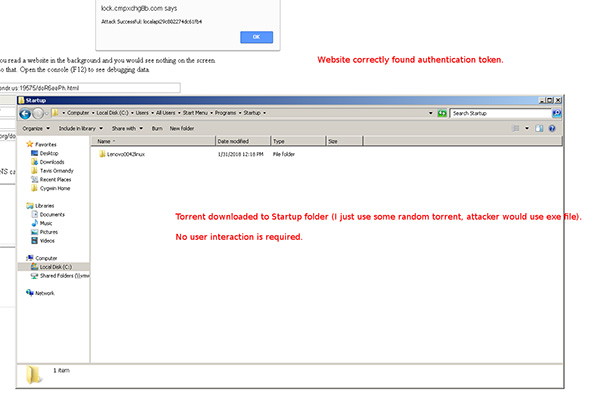
Thankfully, the BitTorrent team has been quick to quell the threat by rolling out builds sans the aforementioned flaws. While the vulnerability-free version of the uTorrent Classic client, v3.5.3 , is still in beta, uTorrent Web has already received a stable update to version 0.12.0.502 with the security patch in place.
If you are using uTorrent’s web variant, we strongly advise updating to the latest version before your next use. uTorrent Classic should have its final build of version 3.5.3 out in the days that follow.
(Source: Project Zero)
You may also like to check out:
- Want Old Snapchat Version Update Reversal On iOS, Android? Here’s How To Do It
- LocationFaker iOS 11 IPA / DEB Download For iPhone Now Available
- Download iOS 11.3 Beta 3 IPSW Links, OTA With CPU Throttling Toggle, New Animoji, And More
- iOS 11.2.6 Jailbreak: Here’s What You Need To Know
- How To Downgrade iOS 11.2.6 On iPhone, iPad, iPod touch
- Download iOS 11.2.6 IPSW Links And OTA With Fix For Messages Crashing Bug
- Jailbreak iOS 11.2.6 / 11.2.5 / 11.2.2 On iPhone And iPad [Status Update]
- Jailbreak iOS 11 / 11.1.2 On iPhone X, 8, 7, iPad Using Electra Or LiberiOS [Updated]
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

