The existence of malware on Apple’s iOS platform isn’t exactly a new thing, contrary to the popular myth that iOS and OS X are bulletproof. With that said, as a mobile platform, iOS is seemingly a lot more secure than the competition, and has historically only come under attack if the device is actually jailbroken, meaning when it has been liberated from the security of Apple’s walled garden. Unfortunately, that may no longer be the case thanks to a new strain of malware known as YiSpecter, which has been discovered to attack non-jailbroken iOS devices.
YiSpecter is a recently discovered malicious form of malware that is the first of its kind. In order to go about its business, the malware uses and abuses a private API in order to gain access to the device and unleash its evil intent. The strain has actually been around for approximately ten months and is currently known to be limited to users in China and Taiwan. YiSpecter manages to spread and gain access to devices through hijacking of ISP traffic, an additional strain of malware on the Windows platform, and offline application installation.

The internal DNA of the YiSpecter malware is quite intricate and involves four different components that have all been digitally signed by various enterprise certificates. Those individual components work in conjunction with one another to set off a chain of downloads that originates from a remote server. The malware is then instructed internally to hide its own icons from the iOS home screen so it doesn’t raise suspicion with the owner of the device. For those that actually have the ability to access hidden icons, the developers behind YiSpecter have attempted to mask the malicious nature of the installation by masquerading it as an official App Store installation.
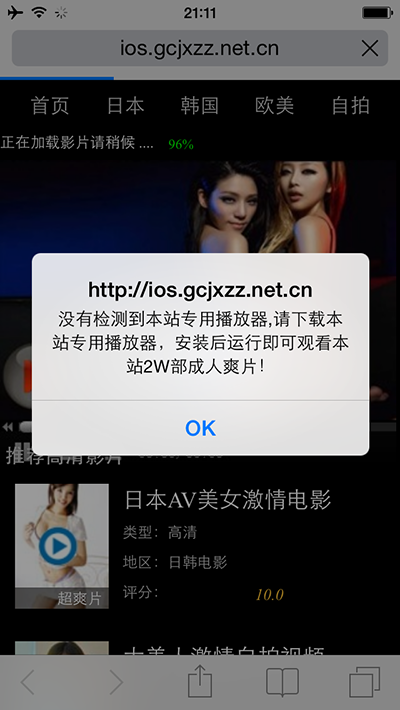
In terms of the underlying intent of the malware, it’s fairly far reaching. YiSpecter is able to change the default search engine in Safari, replace installed apps with ones of its own choosing that have been downloaded remotely to collect data and inputs, as well as upload acquired information to a control center server. It has however been recently discovered that the vulnerability within iOS that allows access to Yispecter, has been patched with the release of iOS 9. To be more clear, it only affects iOS 8.3 and below. iOS 8.4 and above are all safe. Yet another reason for iPhone and iPad users to upgrade to the latest firmware.
(Source: Palo Alto Networks)
You may also like to check out:
- Jailbreak iOS 9, 9.0.2, 9.0.1 Status Update For iPhone And iPad
- Download iOS 9, 9.0.2 And Install On iPhone 6, 6 Plus, 5s, 5c, 5, 4S, iPad, iPod touch [Tutorial]
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

