Cyber security is a big thing these days and it’s only going to get even bigger as we increasingly blur the lines between our digital and physical lives. A particular set of security researchers know that too well, so when they start to warn of malware targeting iOS devices that don’t need to be jailbroken, it’s worth listening to them.
According to the researchers at TrendLabs the particular malware in question was first found on the Windows computers of European defense organizations as well as those of governments and the media. That may not be such a huge surprise given the prevalence of malware on Windows machines, but the news that this particular brand of nastiness is now making its way to iOS will be cause for concern for many.

Dubbed “Operation Pawn Storm,” the malware campaign has found its way to iOS by luring unsuspecting users to install it via the iOS ad-hoc provisioning feature that was designed to allow developers to install their apps without them having to be pushed to the App Store first. All the malware needs to do is get someone to tap a button on a webpage and have them move through some provisioning options and it then has the ability to record voice, send location data and other identifying information back to a central server. Fortunately though it appears that the software was originally designed for iOS 7 and cannot be quite so affective on the newer iOS 8 thanks to its inability to hide itself.
Called the XAgent malware, the software doesn’t need a device to be jailbroken in order to infect it, something that is a relatively new development in the world of iOS malware. Other malware does require that a device already be jailbroken, something that makes its target audience already considerably smaller than that of XAgent.
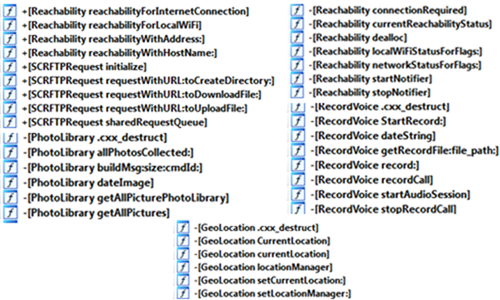
The interesting thing to note here is that we’ve seen a malware of this nature already in the past. For those who might not be able to recall, WireLurker used the same provisioning technique to infiltrate an iOS device, but it did so using a USB cable. Thankfully, the people behind the dreaded malware were arrested and put behind bars.
Let’s just hope the authorities make a swift move regarding XAgent as well.
(Source: TrendLabs)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

