A newly published report is suggesting that iOS users in Japan are being targeted by cyber criminals with a malicious app when they try to view ‘unsafe’ videos. Famously known as the one-click fraud, the scam is not only applicable to jailbroken iOS devices, but non-jailbroken ones as well.
This one-click formula has been around for quite some time now and has been actively used against Windows, Mac, and even Android users in the past few years. The threat to iOS devices was just learnt by Symantec, with the company believing that not only have these scammer prepared an iOS version of the app, but “are distributing it on an identical fraudulent site.”

Over-The-Air delivery of an app this way on iOS is nothing new. Some hackers have been found to abuse Apple’s iOS Developer Enterprise Program in the past. WireLurker is one recent example of this kind of exploitation by hackers, where signed enterprise certificates are used to install a malicious app on a device. The same technique is used by apps such as MovieBox and PlayBox as well for installation. Once Apple revokes the enterprise certificates, the Over-The-Air installation route for these apps cease to work.
“The scammers are likely taking advantage of the iOS Developer Enterprise Program for their campaign, though we have not confirmed this,” says Symantec which further explains that it is the first time the company has seen “a malicious iOS app being used for one-click fraud purposes.”
“If the app is installed on the user’s device, then it tells the user that they have agreed to become a member of the site and demands that they pay 99,000 Japanese yen (approximately US$800) now or 300,000 yen (approximately $2,400) after three days.” The app itself serves as a component to luring in a victim to pay for a subscription.
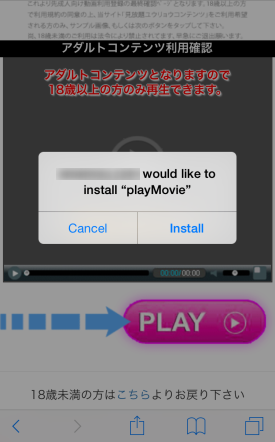
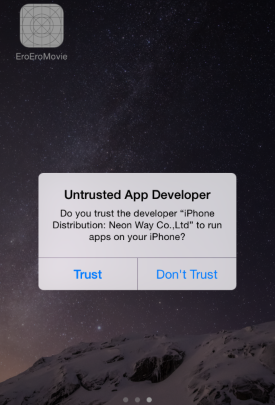
If you see any such strange app asking you to trust and install it OTA via web, as shown in screenshots above, do not accept it unless and until you know and trust the app or its developer. As long as you don’t install such apps from untrusted developers, you will be safe from this malicious app and fraudulent scam.
The iOS Developer Program, which costs $99 annually, allows members to distribute apps using ad hoc provisioning profiles to devices that have their unique IDs (UDID) registered. The iOS Developer Enterprise Program however is more flexible and costs $299 per annum. It uses signed certificates to push apps Over-The-Air. No UDID registration is required for this program. Companies usually use this program to test or install in-house apps on their employees’ devices. The attack discussed above is likely, but not surely, abusing Apple’s iOS Developer Enterprise Program.
(Source: Symantec)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

