The extremely popular Popcorn Time movie steaming app and service may have come in for a lot of criticism since it came into existence but today it faces an attack of a more sinister nature. Rather than being the target for anti-piracy companies trying to get it shut down once and for all, it has now come to the attention of security researcher Antonios A. Chariton who says that a fork of the Popcorn Time app is entirely susceptible to a malicious ‘man-in-the-middle’ attack, that would essentially provide an attacker with entire control over a vulnerable machine.
Popcorn Time has been gaining itself a reputation as one of the most popular free movie steaming apps on the Internet for close to eighteen months now. In that time it has managed to equally divide opinions amongst those who love consuming the content it so easily provides, and those who passionately care about the protection of copyright content and want it shut down permanently. The success of the app seems to be what has driven Chariton to actually do some research on the strength of its security, and find this man-in-the-middle vulnerability.
Chariton decided to investigate Popcorn Time’s vulnerability after a chance discovery when he was setting the app up on his computer. When trying to set up his computer firewall, he noticed some network traffic initiated by Popcorn Time relating to its internal methods used to bypass ISP-level blocking in the United Kingdom; basically code within that app that’s used to prevent Internet providers in the UK from blocking access to Popcorn Time’s services. Chariton explains that:
First of all, the request to Cloudflare is initiated over plain HTTP. That means both the request and the response can be changed by someone with a Man In The Middle position (Local Attacker, Network Administrator, ISP, Government, etc.). The second mistake is that there is no input sanitization whatsoever. That means, there are no checks in place to ensure the validity of the data received. The third mistake is that they make the previous two mistakes in a NodeJS application.
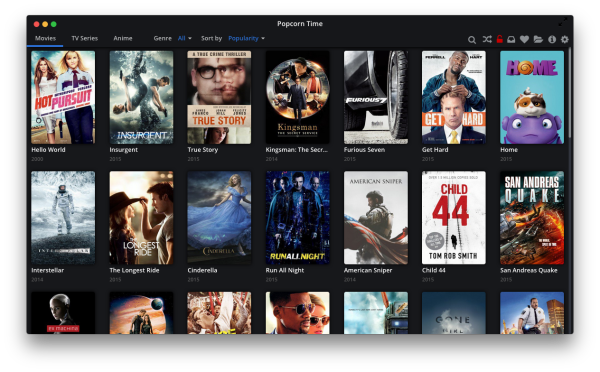
To demonstrate his ability to intercept and change data, Chariton simply changed the title of one movie within Popcorn Time to “Hello World”. Not exactly the most malicious thing you can do but still representative of an attacker’s ability to intercept and manipulate traffic to and from the application. Chariton also demonstrated his ability to inject malicious code into the client application through the use of Cross-Site Scripting (XSS) methods allowing remote code to be executed on any individual’s machine.
The team behind Popcorn Time has responded with the following comments:
This attack requires that the attacker is either inside the local network, inside the host machine, or has poisoned the DNS servers. In any case, there are far more valuable attacks than simply hitting Popcorn Time. Especially because it does not run with elevated privileges and won’t let the attacker install new programs for example.
(Source: TorrentFreak)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

