Google’s Android operating system has never been known for its security, and a video published today wouldn’t help that cause either as it shows just how insecure and vulnerable Samsung Android smartphones are.
As of Android 5.0 Lollipop, Google has embedded a Factory Reset Protection system in Android which protects the device from getting reset to factory state via Recovery mode, stopping anyone from getting access to it. But as this demo video shows, this security layer has been bypassed, at least on the Samsung phones.
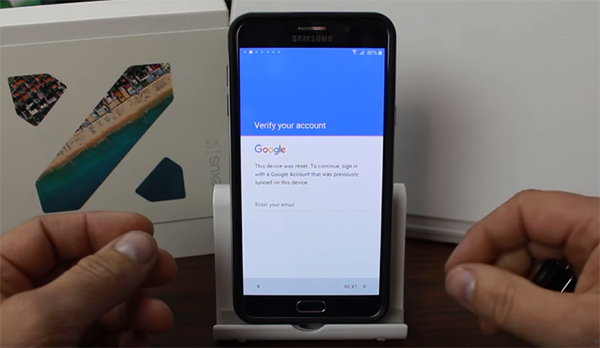
Resetting an Android device via Recovery mode has always been the modus operandi for gaining access to locked phones and tablets, though at the loss of user data such as contacts, messages, email, and other critical information. However this could still leave some data intact in portions of the internal storage that can be accessed pretty easily through various means. The arrival of Android Lollipop was supposed to put a halt on such a thing by asking for the user’s Google account password after a reset from the Recovery has been initiated.
But since Factory Reset Protection is not triggered when the device is reset from the Settings app in Android, and Samsung phones are designed to automatically access any USB OTG storage device when it’s connected, even if the phone is locked, the whole security system can easily be exploited. All that is needed, is a purposed APK file being copied to the USB OTG storage device and then connecting it to the phone, thereby allowing the access to that file without any hindrance. Once you have access to the APK, simply run it and voila! You now have access to the Settings app which was otherwise locked away.
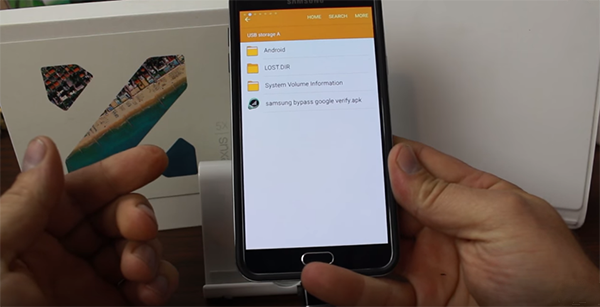
Once in Settings, you can easily reset the phone and not have to face any lock pattern, passcode or Google account password upon reboot. This is obviously a huge security flaw which Samsung needs to fix as soon as possible.
Check out the video below to see just how it all transpires in a few easy steps.
(Source: Rootjunky [YouTube])
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

