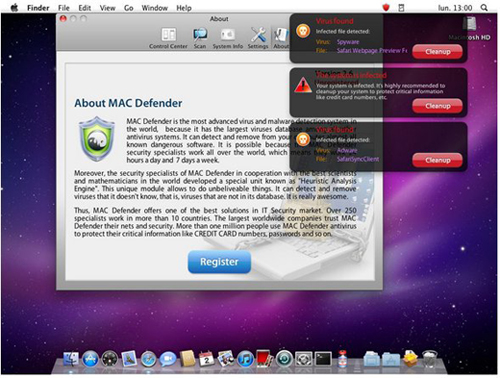
Last week, the Mac community was dead scared when the first widespread Mac OS X malware threat, Mac Defender, sometimes also under other names such as Mac Protector or Mac Security, made its way onto the internet. The malware is distributed through ill-designed webpages that claim that the user’s Mac has been infected.
The original version of the program required users to actually run the rogue program’s installer and type in their administrator password. Sadly, many fell for it and found themselves with their system infected.
Mac users rejoiced when days ago, Apple released a security bulletin warning users of the infection and providing steps to remove the infection, which involve terminating all Mac Defender-related processes and removing all the applications and login items related to the program. The company also promised a security update that would remove the malware and prevent it from being installed to be released "in the coming days".
That reaction, which many believe was too little too late, was good while it lasted. It’s now being reported that another variant of Mac Defender has popped up: this time named ‘MacGuard’, and it’s able to operate without having the user type in an administrator password.
The structure of the program has also changed. The new fake scanner is now divided into two parts: a downloader, which is automatically downloaded from an ill-intentioned website, and will obtain MacGuard itself from a web server, in the background, without the user’s consent. Next thing users knows, they’ll be flooded with pop-up notifications urging them to type in their credit card information, allegedly to make the problem "go away".
As the infection spreads, we’ll need an even quicker response from Apple. Those familiar with OS security know Microsoft went through a similarly rough period in 2003-2004, which forced them to react a lot more quickly in the short run and create better awareness among their customers about security threats in the long-run. Apple might have to do the same and help customers be more proactive as far as malware threats go, since Windows users clearly aren’t the only ones susceptible to malware infections anymore.
It’s important to note, however, that this new version of Mac Defender still requires user interaction in order to function: when the first component is downloaded, users will have to click through a standard Mac installer. That might be enough to dissuade some.
In the short run, one of the ways you can protect yourself would be by unchecking the "Open Safe Files After Downloading" option. That will stop the installer from opening automatically.
(via The Mac Security Blog)
You can follow us on Twitter or join our Facebook fanpage to keep yourself updated on all the latest from Microsoft, Google and Apple.