A security analytics firm has identified a bug within a popular open-source networking library that potentially leaves up to 1,500 apps on the iOS App Store susceptible to malicious attacks. The report on the bug, which was identified last month, claims that apps using a particular version of the extremely popular AFNetworking library could be putting users at risk by exposing sensitive data – such as passwords, bank account information – and making it available to those with the expertise to exploit the vulnerability.
The bright side of the situation is that the open-source code that contains the concerning vulnerability has been fixed almost immediately by the developer behind the project, meaning that any future app submission containing this library should be safe to use. The not so bright side is that approximately 1,500 apps on the App Store are still using the vulnerable version of the project. This is due to the fact that the developers of the affected apps have yet to import the latest fixed version of AFNetworking and resubmit as an update.

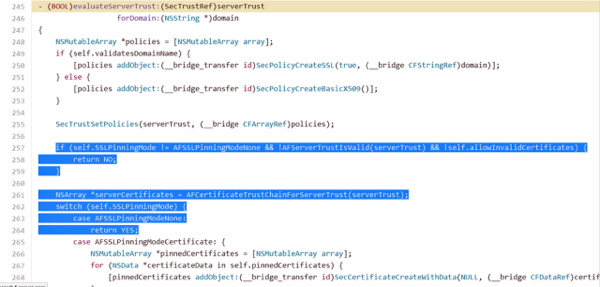
AFNetworking is undoubtedly one of the most popular open-source solutions amongst developers looking for an out-of-the-box networking solution for apps that go and retrieve data from the Web. The project itself has been around for a number of years and is described as “an open-source code library that allows developers to drop networking capabilities into their apps”, with the affected version going live in January of this year. Those apps with the problematic version of the library will be susceptible to man-in-the-middle attacks that essentially allows malicious individuals to intercept and access data encrypted by the HTTPS protocol.
Thanks to a nice little tool living on the Web, it’s possible to search through the affected apps to see if you have any installed on your iOS device. SourceDNA’s iOS Security Report Lookup Tool allows individuals to search for a developer’s name and determine whether or not any of their apps use AFNetworking, and whether those apps with the library installed are actually using the vulnerable version. You can access the tool by going to: searchlight.sourcedna.com/lookup
(via: ArsTechnica)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

