When you think of Apple devices and software, such as iPhones and iPads that run iOS, and Mac computers that run OS X from a security perspective, you tend to think on the more positive side. After all, Mac computers and iOS-powered devices are as secure as can be, right? Recent discoveries have shown that iOS isn’t as secured as consumers may have hoped, and now a newly discovered exploit in OS X has revealed that it’s possible to bypass Apple’s Gatekeeper protection to install malicious apps without a user’s consent.
Gatekeeper first made its appearance on the Mac lineup back in 2012 as part of the OS X Mountain Lion 10.8 release. The Gatekeeper software is essentially designed and bundled with the Mac in an attempt to protect the computer from apps that could otherwise cause harm. Gatekeeper achieves this level of protection by checking the digital certificate that’s bundled with a specific application and evaluating whether or not it’s from an Apple-approved developer or an otherwise trusted source. If not, Gatekeeper blocks the app from running in order to protect the user.

Of course, OS X does have built-in mechanisms in place to bypass Gatekeeper should the user wish to, if for example an app was downloaded from outside of the Mac App Store, but can be trusted. The app can then be manually invoked and the Gatekeeper bypassed. That said, Patrick Wardle, the Director of Research for security outfit Synack, has discovered a flaw in the Gatekeeper that allows an application to bypass checks even with the strictest filtering levels activated.
The process works by utilizing a widely available binary that already includes a digital certificate signed by Apple. Once the binary has been executed, it then runs an entirely different binary located in the same folder in place of the initial Apple-signed file. The attack works by renaming the initial binary and packing it inside an Apple disk image, and because Apple has signed the binary, Gatekeeper sees no harm in approving the process and allows it to execute.
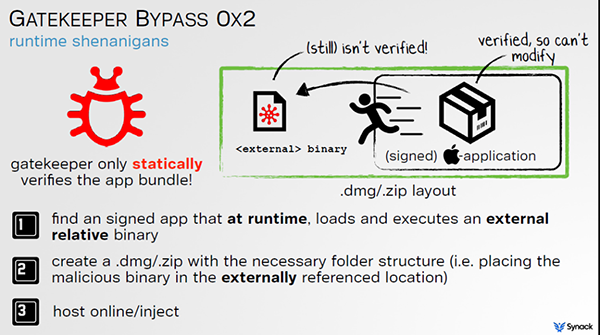
It’s not super complicated, but it effectively completely bypasses Gatekeeper. This provides hackers the ability to go back to their old tricks of infecting users via Trojans, rogue AV scams or infect applications on Pirate Bay. More worrisome to me is this would allow more sophisticated adversaries to have network access. Nation states with higher level access, they see insecure downloads, they can swap in this legitimate Apple binary and this malicious binary as well and man-in-the-middle the attack and Gatekeeper won’t protect users from it anymore.
Apple has already been informed about the Gatekeeper vulnerability. Wardle and Synack believe that the Cupertino-based outfit is currently working on a potential fix for the issue, as an Apple spokesperson has since confirmed that internal engineering teams are working on a solution but no timescale has been offered for when it will be pushed out.
All versions of OS X, including the latest El Capitan, are affected by this.
(Source: Threatpost)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

