iOS hacker iH8sn0w has discovered a way to untether jailbreak devices powered by the Apple A5(X) processor for life, which includes the iPhone 4s, iPod touch 5, the iPad 2 / 3 and iPad mini. Details are relatively scarce at this moment regarding the iBoot exploit, although if the exploits were ever bound together and released in the form of a jailbreak utility, those in ownership of either device would be able to enjoy an potentially indefinite, untethered jailbreak.

Even though the jailbreak scene is very much a here-and-now kind of pastime in that most enthusiasts are keen to find way to breach the latest versions, it’s always nice to see progress of any kind. And by the sounds of things, this is a pretty significant inroad. Taking to his Twitter feed, iH8sn0w posted A5 AES keys:
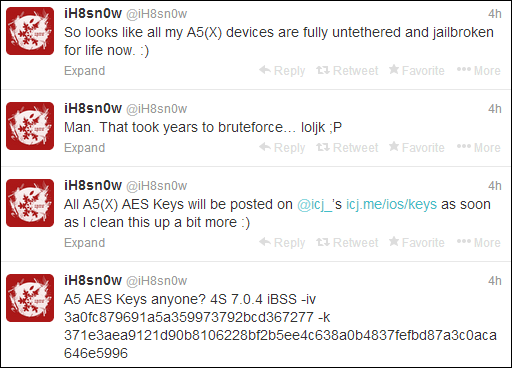
So looks like all my A5(X) devices are fully untethered and jailbroken for life now.
A5 AES Keys anyone? 4S 7.0.4 iBSS -iv 3a0fc879691a5a359973792bcd367277 -k 371e3aea9121d90b8106228bf2b5ee4c638a0b4837fefbd87a3c0aca646e5996
All A5(X) AES Keys will be posted on @icj_’s icj.me/ios/keys as soon as I clean this up a bit more 🙂
Then, in speaking to fellow hacker Winocm, one of the guys behind p0sixspwn, iH8sn0w offered something of an insight into how exactly he managed to work the magic:
This isn’t a bootrom exploit. Still a very powerful iBoot exploit though (when exploited properly ;P /cc @winocm).
One follower also noted that iBoot jailbreaks can be patched by Apple on the fly. iH8sn0w responded to this by noting that they can be patched provided that they are released publicly.
Also, to further add fuel to this argument, Saurik took to a thread on Reddit to shed some light on the situation:
For informational purposes (as many people reading might not appreciate the difference), to get the encryption keys you only need an "iBoot exploit", not a "bootrom exploit". It is easier to find iBoot exploits (being later in the boot sequence, it has a larger attack surface: it has to be able to parse filesystems, for example), and they do afford more power over the device than an untethered userland exploit (in addition to letting you derive firmware encryption keys, you can boot custom kernels, and you might be able to dump the bootrom itself), but they are software updatable as part of new firmware releases from Apple and may have "insane setup requirements" (like, you might pretty much need an already-jailbroken device to actually setup the exploit). You thereby wouldn’t see an iBoot exploit used for a jailbreak (unless everyone is out of ideas for a very long time): instead, you’d see it hoarded away as a "secret weapon" used by jailbreakers to derive these encryption keys, making it easier to find and implement exploits on newer firmware updates for the same device (especially kernel exploits, where even if you have an arbitrary write vulnerability you are "flying blind" and thinking "ok, now where should I write? I can’t see anything… :'(").

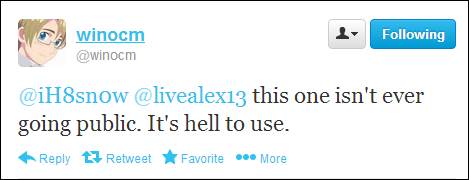
But the big question is: will the exploit ever go public? Sadly, it won’t, according to a tweet by Winocm.
There’s no doubt that this is very exciting news, and we’ll be keeping a close eye on what remains a developing sequence of events, so stay tuned!
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

