By and large, jailbreaking is a relatively safe affair to perform, and as long as you abide by the precautionary steps that must be taken when opening areas of the ecosystem ordinarily shut off by Apple, you’re generally safe. However, given that third parties can access root files, things can sometimes go horribly wrong, and with the jailbreak scene having been afflicted by two widespread incidents in the past five months, another piece of malicious software is said to be capable of stealing your Apple ID and password to buy apps without your consent.
Named AppBuyer by the Palo Alto Networks team that discovered it, their report on the new malicious code is both extensive and makes for rather disconcerting reading for jailbreakers far and wide. Apparently, AppBuyer will connect to a C&C server before downloading and executing malicious codes. It can then swipe network APIs and in turn, snap up a user’s Apple ID and password.

The process has been constructed as such that it will then “simulate Apple’s proprietary protocols” to buy apps using these ill-obtained credentials.
The guys behind the Unflod.dylib malware back in April used a presumably similar technique to avail the same result; that is, to glean Apple ID data. But while the Cupertino company has faced some stiff questions recently regarding the security of its iCloud infrastructure, Apple tends to wash its hands of any issues that arise via jailbreaking, which, by the way, the company is not an advocate of.
As well as releasing a detailed report on how AppBuyer works, Palo Alto Networks also releases some information on how one may be able to check and see whether a jailbroken device has been infected.
Using any file browsing tool (we always recommend iFile), you should check to see if any of the following files exist on any of your jailbroken devices:
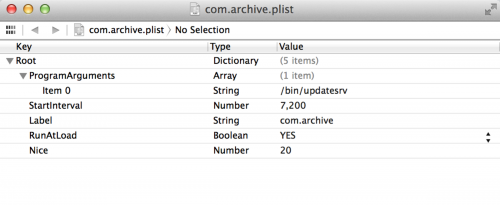
/System/Library/LaunchDaemons/com.archive.plist
/bin/updatesrv
/tmp/updatesrv.log
/etc/uuid
/Library/MobileSubstrate/DynamicLibraries/aid.dylib
/usr/bin/gzip
If any of the above files are present, then a device may well be infected by AppBuyer. With that said, the guys at Palo Alto Networks also concede that at present, “we still don’t know how the AppBuyer got onto the device, just deleting these files may not solve the problem completely.”
It’s another major blow for a community that has been rocked by such outbreaks in recent months. As well as the aforementioned Unflod.dylib, AdThief also reportedly hit 75,000 jailbroken devices. If you’re a jailbroken iOS device user, we suggest avoiding tweaks from untrusted and pirated Cydia repositories. Stay safe!
(Source: PaloAltoNetworks) (via: Reddit)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the web.

